Lightweight Vulnerability Scanning with Cloudflare's Flan Scanner
This post will just contain some notes on using Cloudflare’s Flan scanner for extremely lightweight yet professional and reliable vulnerability scanning.
I wrote this as I wanted a lightweight but reliable method for conducting vulnerability scans on something as underpowered as an Android phone. Since Flan relies on nmap, the vulners nmap plugin and Python, this workflow could pretty much run on any device that supports those three tools.
This post uses Unix commands so if you’re on Windows use something like WSL2 if you want to copy/paste the snippets, otherwise just plan on modifying the snippets for Powershell’s syntax.
Setup:
Install Docker on your scanning host.
Running Flan:
I created a Docker image for Flan, you can check out the Dockerfile here: flan-scan Dockerfile
The following commands should be fairly self-explanatory if you know Unix command syntax at all so I will not be explaining each step, just modify the IP ranges needed in /tmp/ips.txt (separating CIDR ranges by newlines in the file):
mkdir -p /tmp/flan-scan
cd /tmp/flan-scan
mkdir reports
mkdir xml_files
printf '192.168.50.0/24\n' >> /tmp/ips.txt
Then run the Docker container to do the scan:
docker run --rm \
--name flan-scan \
--network=host \
-v /tmp/ips.txt:/shared/ips.txt \
-v $(pwd)/flan_scan/reports:/shared/reports \
-v $(pwd)/flan_scan/xml_files:/shared/xml_files \
-e format=html \
heywoodlh/flan-scan
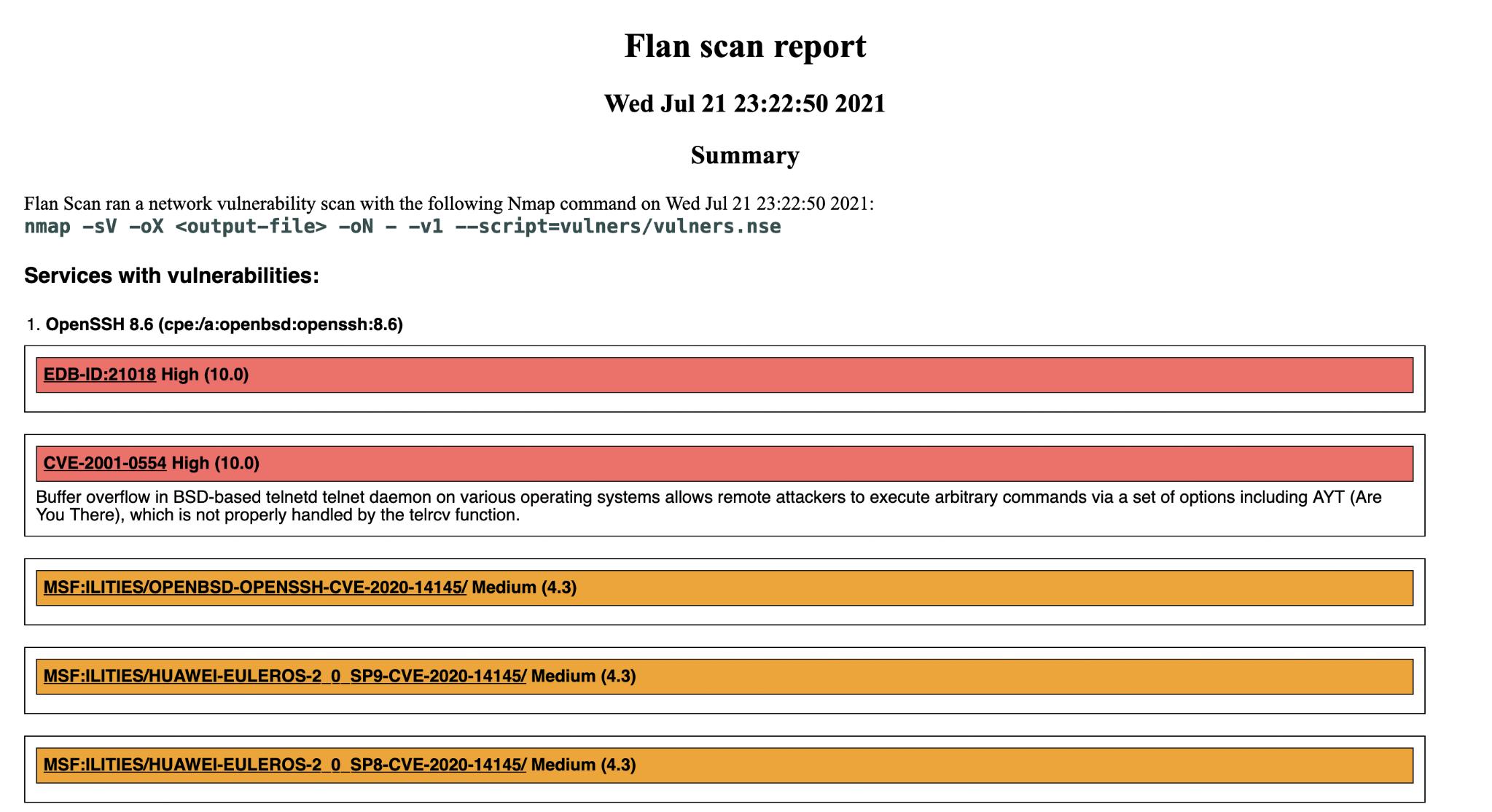
Once the scan completes it should place an HTML file in /tmp/flan_scan/reports/ with the results.
Here’s my BASH function for flan:
Here’s an example HTML file from a scan I ran just before writing this: